Whilst we’ve explored some ‘normalised’ ways to electronically intrude on your friends, potential partners and loved ones. There are a number of terrifying mobile applications that one could physically install on a partner’s phone for the purposes of electronic intrusion.
Feel free to browse through the apps/tools below (the links open in new tabs). They range from mildly unethical to how-is-this-legal?! unethical:
| Designed for intrusion | Not designed for intrusion |
Scary, right?
I suppose there are some weird legal loopholes/grey areas at play here. As I said, some of these apps technically need to be installed on the host phone, so it would require the primary user to physically download it. I’ll make a blanket generalisation and assume that everyone has a passcode/fingerprint protected phone these days. However, some partners/friends trust each other enough to exchange these (passcodes – not fingers! Dear God).
It does make me wonder if there have been court cases based on this type of intrusion? (Perhaps I’ll expand on current Australian stalking laws in a later blog post).
What about data security?

If these companies storing our phone calls, messages, photos, GPS locations on their servers, what precautions are they taking to protect this data?
Good question.
I came across this notice when I visited the Retina-X Studios website (the creators of mSpy).
“IMPORTANT NOTE: 03/05/18: Regrettably Retina-X Studios, which offers cutting edge technology that helps parents and employers gather important information on devices they own, has been the victim of sophisticated and repeated illegal hackings. Over the past year, Retina-X Studios has begun to implement steps designed to enhance our security measures which had the positive outcome of restricting data obtained by the hackers in the most recent intrusion. No personal data was accessed, but some photographic material of TeenShield and PhoneSheriff customers has been exposed” (Retina-X Studios, 2018)
And apparently this wasn’t the first time Retina-X had been hacked either…
These servers are treasure troves of information – all fuelled by our need to control and calm our anxieties. What is happening to our world and to the way we treat each other? There is literally an industry built off our desires to spy on each other.
Legitimate use cases?
Trying to provide a balanced view here – I suppose there are some legitimate use cases for these intrusion apps? What if you wanted to protect the type of content your child was viewing on their smartphone? Or check in to see their location to make sure that they were safe.
Valid points, yes.
However, there are ways around this. Children are pretty smart these days and probably know how to operate GPS relocation apps. (There were quite a number of people that did this to ‘hack’ Pokemon Go when it was first released back 2016 in order to catch rare Pokemon). So why bother?
I’ve gotten a little off track from my main point. Let’s get back on the wagon.
CheaterBuster

The app that strikes me the most is CheaterBuster (formerly SwipeBuster). Why you ask? Because it doesn’t require you to physically install the application in order to search through sensitive data.
So, what are its features?
CheaterBuster allows you to search and view Tinder profiles. All you need is a first name, age (approximate) and location. It is a paid service and costs $7.49, plus tax (US dollars) for 3 searches.
This app was originally created for the purpose of ‘busting’ cheating partners, but it makes me wonder what other purposes could it be used for?
The one that got away…
What if you decided to use this app not to check up on your partner, but rather, to chase the one that ‘got away’.
Rejection hurts, but what feels better – justice? Revenge? Or perhaps elaborate plots to ‘bump’ into this person?

Anything is possible I suppose.
You could potentially use Cheaterbuster to keep tabs on a person’s profile changes and start to form a collection of information, including
- Places they frequent (like bars, cafes etc, deduced from photo information)
- Places they work
- Location based hobbies or interests
This could be then cross referenced with social media profiles such as Facebook, Instagram (often this is linked in Tinder), LinkedIn, Google and Twitter.
For instance if they have left a review on a cafe that they frequent, then you could check their Google profile and all of the places that they regularly visit.
Below is a diagram I quickly whipped up. As you can see, it doesn’t take much to quickly build a network of information on someone.
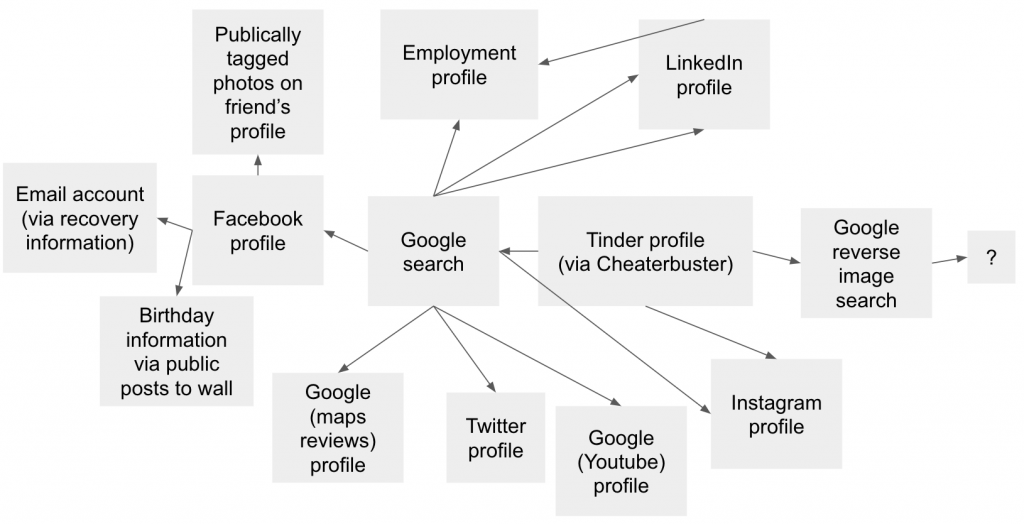

Cheaterbuster could also be used to indicate whether a person had deactivated their account, which might indicate that they’ve since found a partner.
Ethics?
At this point you’re probably wondering how can Tinder ethically divulge this information?
Well, have you heard of something called an API?
APIs
API stands for ‘application programming interface’. Redhat (2019) defines an API as “a set of definitions and protocols for building and integrating application software…APIs let your product or service communicate with other products and services without having to know how they’re implemented.”
If that hurt your brain and you’re still not sure, have a watch of this short video below.
Many tech companies use APIs for a number of different reasons and they’re all not bad. For instance, Facebook has an API which allows organisations to link your existing profile to their database to avoid that dreaded ‘sign up fatigue’. (Similarly, Google, Twitter and WordPress have these integrations available as well).

An example of the Tinder app’s API usage is through ‘bots’ or artificially intelligent profiles. Whilst it’s not a great use of the service, I can imagine Tinder welcomes this ‘illusion of abundance’, making it seem like the app offers far more women than in reality.
What I’m trying to say is, the dispersal of this information is all completely legal and outlined in Tinder’s terms and conditions on sign up.
So, should we be taking precautions?
Welp, for starters, nothing you post on your Tinder profile is safe.
Especially your images.
In fact, a GitHub user by the name of Scoliann (alongside many contributors) wrote a program in 2017 called TinderFaceScraper that built a ‘facial dataset’ of 40,000 images pulled from Tinder’s API (Neal, 2017).
The repository has been since removed after violating Tinder’s copyright policy, but it got me thinking about Google reverse image search. Anyone could just screenshot your photos, use reverse image search and uncover more information about you.
Who’s to know if employers are out there watching profiles?
I’m not here to fear monger, rather, provide some food for thought.
What’s to come?
Many questions come to mind, but I need your help answering them…
How does the freedom to electronically intrude on our loved ones affect us? Is this just the norm now? Can we trust our loved ones and random strangers on Tinder? Should we be mindful of what we post to our Tinder profiles?
I’d love to hear your thoughts in the comment section below.
Like I said, I’m not here to frighten you (or teach you how to intrude). But it is becoming clear that these companies don’t care about ethics or the right to personal privacy.
They care about their bottom line.
_______
References
Neal, ‘Tinder wants to know how someone swiped 40,000 profile pics in a bad way’, The Inquirer, retrieved 5 June, 2019, <https://www.theinquirer.net/inquirer/news/3009320/tinder-wants-to-know-how-someone-swiped-40-000-profile-pics-in-a-bad-waay>
Redhat 2019, ‘What is an API’, Redhat, retrieved 5 June, 2019 <https://www.redhat.com/en/topics/api/what-are-application-programming-interfaces>
Retina-X Studios 2018, Home page, retrieved 5 June, 2019, <http://www.retinax.com/>
All images featured in this blog post are in the public domain and have been sourced from pixabay.com.

